This is the beginning of an article series about Visual Studio Code. The first step is to download and install it.


This is the beginning of an article series about Visual Studio Code. The first step is to download and install it.

This tutorial shows how to use and collect coverage data using the GNU gcov tool. As board and hardaware I’m using the NXP i.MX RT1064 EVK:

While this tutorial uses this specific board, things are pretty generic and should be applicable for any other board or MCU.
Continue readingIf you are a regular reader of my articles, you probably know that I’m using FreeRTOS in most of my applications, for obvious reasons. But clearly this is not the only RTOS out there. After Microsoft had acquired Express Logic back in April 2019 things kept quite for a while. To me the crown jewel of Express Logic is the ThreadX RTOS. But recently Microsoft is pushing more and more the ‘Azure Sphere’ and trying to monetize the ‘IoT’ (I apologize for mentioning that overused acronym) application space and providing it now free for devices from selected partners which includes NXP now.
Eclipse has a great built-in source code parser and browser (aka ‘Indexer’). It is basically a built-in compiler which parses the source files and assists the user with code completion and navigation help, making Eclipse this awesome productivity tool. On the downside this background parsing could potentially slow down things, and therefore Eclipse has some default settings to prevent this. Unfortunately, the FreeRTOS Kernel ‘tasks.c’ file is above-and-beyond of a ‘sane’ source file and will hit the default limits: as a result the ‘tasks.c’ file is not indexed and things like ‘Open Declaration‘ might not work for the file ‘tasks.c’.
Typically I have many, many projects listed in the Eclipse Project Explorer, usually more than 100 projects: from example projects, projects on git, lecture module projects, research projects or just some hobby projects I’m working on. With the default Eclipse settings, all these projects are listed in a ‘linear’ list. What I found really useful is the ability to group them into ‘Working Sets‘:
It is always great to see if someone is picking up my work and produces something even better :-). In this case, Gerhard Székely took my DIY Portable Video Conference, Sharing and Teaching Device and created an awesome version of it:
COVID-19 is by far not over, and in Switzerland the infection rate is going up again (2nd wave?). During the spring 2020 semester university lock-down we moved pretty much everything to a ‘distance learning’ setup. With that experience and with the request to prepare for the fall semester, I have constructed a DIY conference and teaching device which should make things simpler and easier: a combination of video camera, speaker phone and a muting device:
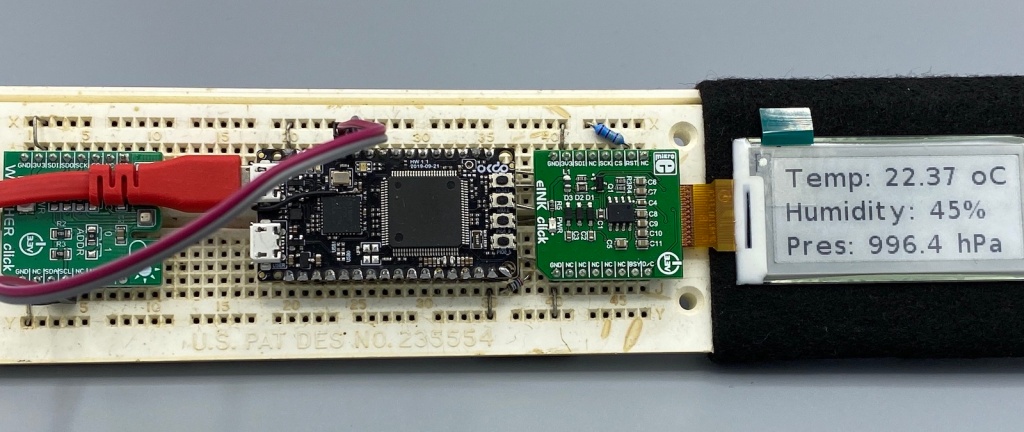
In an earlier tutorial I introduced using I2C with the NXP LPC55S69 on OKdo E1 board to read a Bosch BME280 environmental sensor on a Mikroe Weather Click board. The MCUXpresso Clocks, Pins and Peripheral Config tools were used to get it running. It’s all for my Weather Station project that I’ve been working on during these months of lockdown. It is starting to take shape – as you can see from the photograph:
Now I really need to start reading and writing to the BME280 sensor, and that means using the I2C driver in the lpcxpresso55s69 SDK. And so this week I’ll provide a forensic examination of the most commonly-used I2C function call.
Continue readingI want to share with you a little embedded trick that I use to improve the reliability of my code. And in addition to improving reliability, the technique can be used to schedule any event to occur ‘sometime in the future’. It uses the MicroTick (UTICK) timer found on the NXP LPC55S69 microcontroller, and could be applied to any device with a simple timer.
The MicroTick timer is an elegant, thing of beauty. But there is not a driver example built into the lpcxpresso55s69 SDK, and I believe that the timer is not widely used. That means we need a tutorial!
Continue readingI selected the Bosch BME280 environmental sensor as the heart of my OKdo E1-based weather station. It is convenient to use, and I can prototype with the Mikroe Weather Click board MIKROE-1978. But the sensor is accessed over I2C, and that is my least favourite of the communication interfaces. In this short tutorial, I show you how the MCUXpresso Config tools (Pins, Clocks, Peripherals) are used to set up the I2C driver from the MCUXpresso lpcxpresso55S69 SDK. And very quickly, I am able to communicate with the BME280 sensor.
