For a university reasearch project I try to pair the Raspberry Pi 3 with a Mikroelektronika Hexiwear using BLE (Bluetooth Low Energy). Most of things worked after a lot of trial and error, but at a certain point I was stuck trying to write to send data from the Raspy to the BLE device.The Hexiwear BLE protocol description is very thin, so I ended up using a BLE sniffer to reverse engineer the protocol with Wireshark.
Outline
In this article I describe the needed steps to record and analyze BLE communication packets with the Adafruit Bluefruit LE Sniffer and Wireshark. While I’m using a Raspberry Pi and with the Hexiwear, the steps could be easily applied to any BLE communication. As a special point, I’m sniffing a connection with authentication between the Raspberry Pi and the Hexiwear.
Wireshark is an open source packet sniffing program, for all kind of protocols and packets. With Wireshark and can collect and analyze the BLE packets:
The Adafruit Bluefruit LE Sniffer is a small dongle with serial interface featuring a Nordic Semiconductor nRF51822 BLE module (MDBT40). Adafruit has a module available with a sniffer firmware preloaded (https://www.adafruit.com/product/2269).
Installation
Follow the steps described in https://learn.adafruit.com/introducing-the-adafruit-bluefruit-le-sniffer. I’m using the following:
- FTDI driver for the FT231X on the sniffer: FTDI Driver Download Page
- Nordic Sniffer application (sorry, Windows only): http://www.nordicsemi.com/eng/Products/Bluetooth-low-energy/nRF-Sniffer.
For Mac OS X and Linux see the Adafruit page using the Python API. - Wireshark Version 1.12.10. It is important to use exactly that version, as other versions might not work. The version 1.12.10 can be found here: https://www.wireshark.org/download/https://www.wireshark.org/download/win32/all-versions/ (32bit) and https://www.wireshark.org/download/win64/all-versions/ (64bit)
I’m using the following version of the Nordic Sniffer Software:
This is the version information of the Wireshark version I’m using:
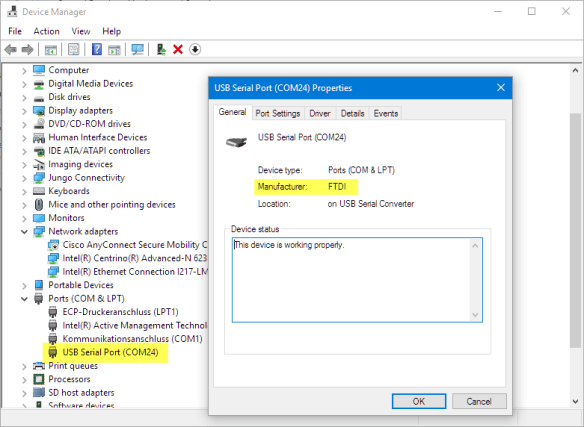
Verify that the FTDI serial driver is installed and the sniffer board is recognized:
Sniffing Encrypted BLE Packets
In order to be able to sniff an encrypted/authenticated connection, it is important to keep the following steps in exact the order presented!
Run the Nordic sniffer application (in my case: ble-sniffer_win_1.0.1_1111_Sniffer.exe):
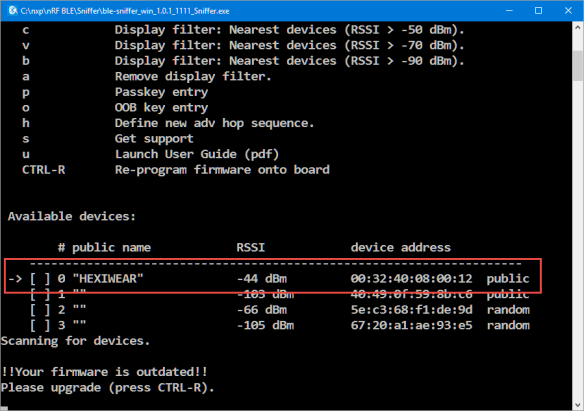
💡 IMPORTANT: the sniffer will report “!!Your firmware is outdated!!”. Do NOT upgrade the firmware!
After a while, the Hexiwear should show up. At that point, start Wireshark with pressing the ‘w’ key in the sniffer:
In the sniffer program, select the Hexiwear device from the list (‘0’ in my case):
Next, start the pairing to the device (see “Tutorial: BLE Pairing the Raspberry Pi 3 Model B with Hexiwear” how to do this from a Raspberry Pi/Linux with Bluez): a pairing code will show up on the device:
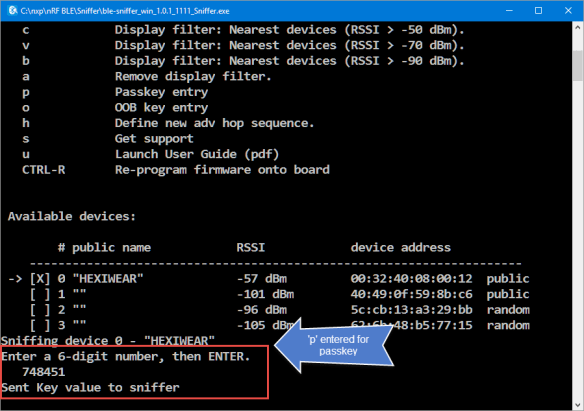
Enter that code first in the sniffer program. For this, enter ‘p’ followed by the passkey.
Then enter that code on the device which initiated the paring (e.g. the Raspberry Pi):
💡 Note that this needs to happen rather fast, as otherwise the pairing will run into a timeout. You might need to try this several times until the sequence works.
With this, the sniffer program and Wireshark can listed to the encrypted data packets.
Filtering Packets
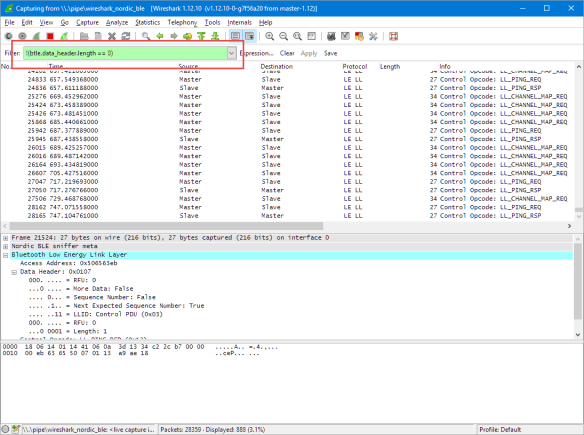
In Wireshark, there are many ’empty PDU’ packets sniffed. The Master (Raspberry Pi in my case) needs to poll the slave, and this results in many empty packets. As I’m not interested in these empty packets, and can filter them out:
Unfold a data header, drill down to the data header length and apply a filter as ‘not selected’:
This removes all the empty PDU packets with a filter:
Inspecting Packets
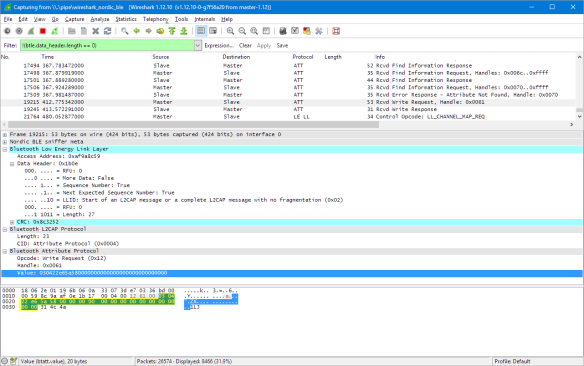
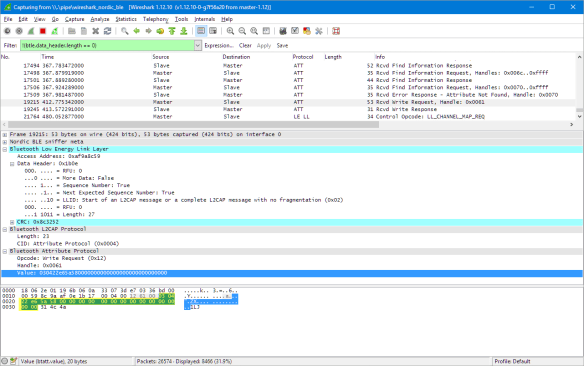
Now I can see in Wireshark the packets. This is very useful for reverse engineering the protocol, or as in the case of the Hexiwear the protocol is not very well documented. For example in “Tutorial: BLE Pairing the Raspberry Pi 3 Model B with Hexiwear” I wanted to write the date/time to the Hexiwear device, but always failed. With Wireshark and the BLE sniffer I was able to record the data packets sent between the mobile phone application and the Hexiwear to set the date/time:
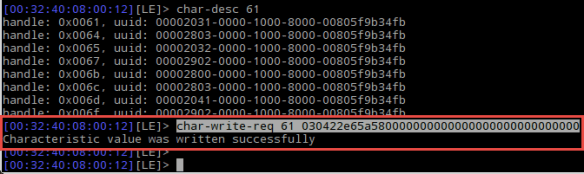
The sniffer shows that the following data is written with a write-request on handle 0x61:
03 04 22e65a58 0000000000000000000000000000
The 0x03 is the command for writing date/time, followed by 0x04 with the length of the following time (seconds since 1970): 0x585ae622 (data is sent in little-endian).
0x585ae622 (or 1482352162) is 21-Dec-2016 20:29:00 (see http://www.epochconverter.com/) which indeed is what showed up on the Hexiwear :-).
With this knowledge, I was able to replicate this from the Raspberry Pi:
char-write-req 61 030422e65a580000000000000000000000000000
Summary
Sometimes it is all about the right tools: like having a logic analyzer to see what is going on with a wired bus like SPI or I²C, a packet sniffer is incredible valuable to understand a wireless protocol. With the help of the Adafruit Bluefuit LE Sniffer and Wireshark I’m now able to inspect and see the encrypted packets exchanged between a Hexiwear and a Raspberry Pi and reverse engineer the protocol used :-).
Happy Sniffing 🙂
Links
- Wireshark: https://en.wikipedia.org/wiki/Wireshark
- Wireshark versions: https://www.wireshark.org/download/win32/all-versions/ and https://www.wireshark.org/download/win64/all-versions/
- Adafruit Bluefruit LE Sniffer: https://www.adafruit.com/product/2269
- Paring Hexiwear with Raspberry Pi: Tutorial: BLE Pairing the Raspberry Pi 3 Model B with Hexiwear








Pingback: Tutorial: BLE Pairing the Raspberry Pi 3 Model B with Hexiwear | MCU on Eclipse
Pingback: Using Python, Gatttool and Bluetooth Low Energy with Hexiwear | MCU on Eclipse
Pingback: Hexiwear | Hexiwear, BLE and sharks – tutorial on BLE communication packets - Hexiwear
Pingback: Using Python to Store Data from many BLE Devices | MCU on Eclipse
You jumped over how to implement Wireshark, going straight from selecting the device in Sniffer over Wireshark configuration and connection, to altering filter settings. I ask because I don’t see the device in my Interface List and wonder if I am missing a step?
LikeLike
Hi Dan,
you have to use the exact version of Wireshark listed in this article. Plus the Adafruit BLE dongle has to be recognized by your system. Make sure you have the proper serial drivers installed and it shows up in your device manager with a virtual COM port.
I hope this helps,
Erich
LikeLike
Hi Erich,
I am wondering if the onboard Bluetooth on the raspberry pi 3 could be used for sniffing Bluetooth signals? Is there any software tool that does that? Thanks
LikeLike
Yes, the hardware certainly supports this, but I have not done it that way. Running it on a PC host was the easiest way to do it.
LikeLike