Binary files are just a binary blob without debug information. Most debug tools and flashers are able to deal (raw) binary (see “S-Record, Intel Hex and Binary Files“). But GDB or the P&E GDB server really needs a ELF/Dwarf file which usually has all the debug information in it. This is a problem if all what I have is a binary file.
This post is about transforming a raw binary (.bin) file into an ELF/Dwarf file with adding a header to it:
I can make a elf file out of a bin (raw binary) file with the GNU ‘objcopy‘ command like this:
arm-none-eabi-objcopy.exe --input-target=binary --output-target=elf32-little myApp.bin myApp.bin.elf
‘myApp.bin’ is the application binary file and it adds an ELF/Dwarf header file to the output file myApp.bin.elf. I can inspect/verify with the ‘readelf’ GNU program:
arm-none-eabi-readelf.exe -a myApp.bin.elf
which gives for example:
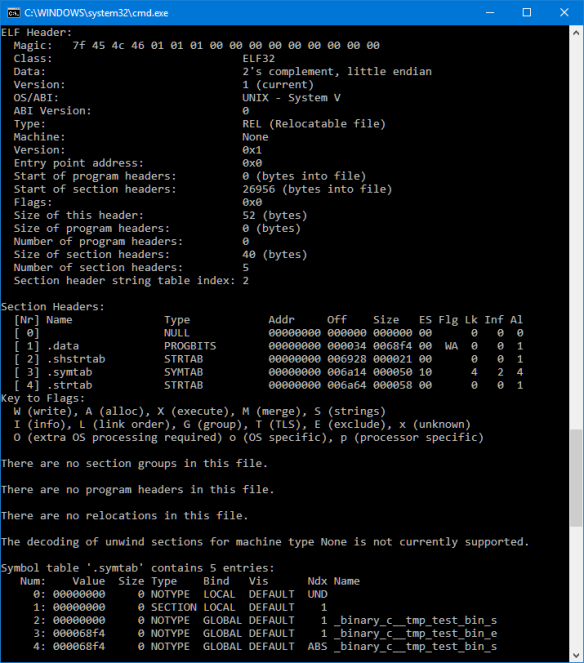
ELF Header: Magic: 7f 45 4c 46 01 01 01 00 00 00 00 00 00 00 00 00 Class: ELF32 Data: 2's complement, little endian Version: 1 (current) OS/ABI: UNIX - System V ABI Version: 0 Type: REL (Relocatable file) Machine: None Version: 0x1 Entry point address: 0x0 Start of program headers: 0 (bytes into file) Start of section headers: 26956 (bytes into file) Flags: 0x0 Size of this header: 52 (bytes) Size of program headers: 0 (bytes) Number of program headers: 0 Size of section headers: 40 (bytes) Number of section headers: 5 Section header string table index: 2 Section Headers: [Nr] Name Type Addr Off Size ES Flg Lk Inf Al [ 0] NULL 00000000 000000 000000 00 0 0 0 [ 1] .data PROGBITS 00000000 000034 0068f4 00 WA 0 0 1 [ 2] .shstrtab STRTAB 00000000 006928 000021 00 0 0 1 [ 3] .symtab SYMTAB 00000000 006a14 000050 10 4 2 4 [ 4] .strtab STRTAB 00000000 006a64 000058 00 0 0 1 Key to Flags: W (write), A (alloc), X (execute), M (merge), S (strings) I (info), L (link order), G (group), T (TLS), E (exclude), x (unknown) O (extra OS processing required) o (OS specific), p (processor specific)
Now I can use that file like any normal ELF/Dwarf file (of course it does not have debug information in it), e.g. see Using Eclipse to Program Binary Files to an Embedded Target.
That’s all :-).
Happy Binaring 🙂

Pingback: Using Eclipse to Program Binary Files to an Embedded Target | MCU on Eclipse
Erich, this is a really good help, thank you. I was wondering if it was really possible to load bin file for P&E like the other post. It used to work but it does not anymore?
Have a nice day!
LikeLike
Hi Diogo,
Yes, I believe it worked, but I’m not sure any more. I see that with the latest version it just does not load anything, so the binary running on that target is not changed. I might have been fooled by that and did not realize that it did not load the binary file? I’m really not sure anymore.
Erich
LikeLike
Hi Erich,
This is very helpful! However, I am wondering if there is a way to stitch together several binaries which represent different sections of memory into a single elf file and still have it work with GDB?
LikeLike
Not that I am aware of.
I don’t think this will be easily possible, at least if you are talking about stitching together multiple ELF files. It would be possible to combine the raw binary (code and constant data) with the approach listed here (combine the binaries first, then wrap it in a .elf file). The problem will be with the debug information which is more of a linker part. For example it would need to check about duplicated symbols, combine the DWARF information, etc.
And that DWARF information is what you need for ‘debugging’, otherwise the debugger has no symbols.
Or you could add the needed symbols as outlined in https://mcuoneclipse.com/tag/add-symbol-file/
I hope this helps,
Erich
LikeLike
Pingback: Reverse Engineering of a Not-so-Secure IoT Device | MCU on Eclipse